We’ve been upgraded: CreativeTechs is now an Apple Premium Technical Partner
Have Your Online Passwords Been Stolen? Here’s How to Find Out.
Data breaches have become commonplace, with online thieves constantly breaking into corporate and government servers and making off with millions—or even hundreds of millions!—of email addresses, often along with other personal information like names, physical address, and passwords.
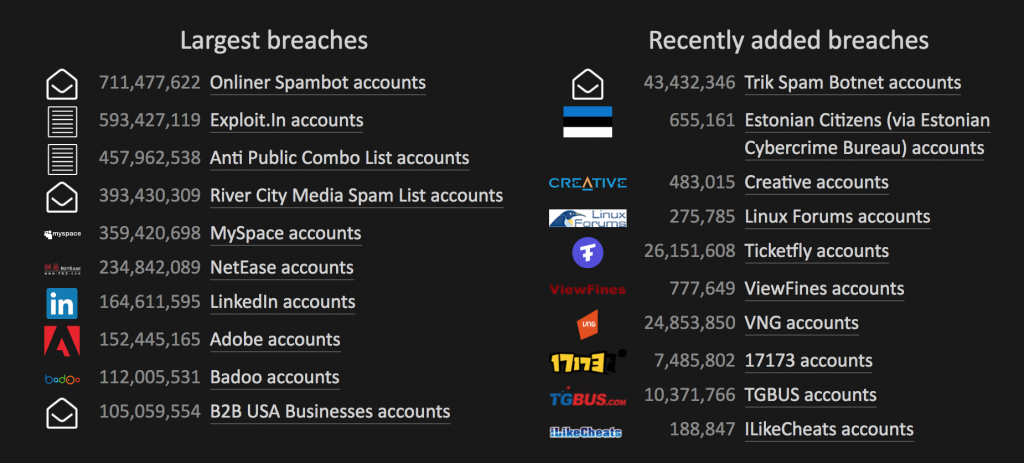
It would be nice to think that all companies properly encrypt their password databases, but the sad reality is that many have poor data security practices. As a result, passwords gathered in a breach are often easily cracked, enabling the bad guys to log in to your accounts. That may not seem like a big deal—who cares if someone reads the local newspaper under your name? But since many people reuse passwords across multiple sites, once one password associated with an email address is known, attackers use automated software to test that combination against many other sites.
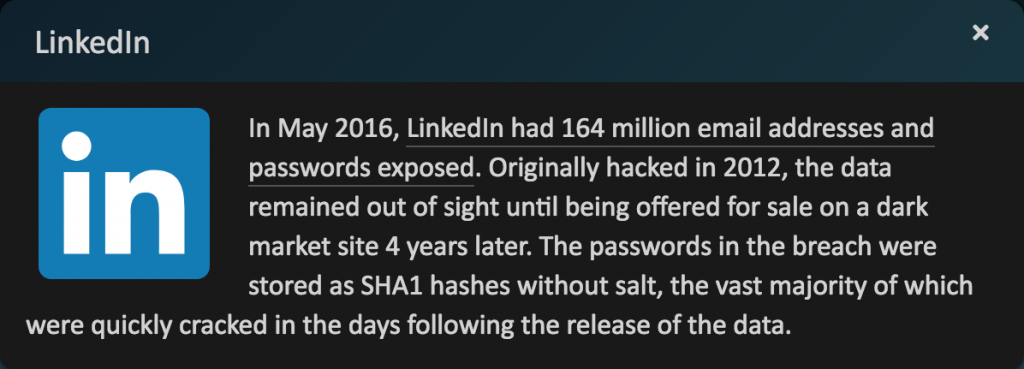
This is why we keep beating the drum for password managers like 1Password and LastPass. They make it easy to create and enter a different random password for every Web site, which protects you in two ways.
- Because password managers can create passwords of any length, you don’t have to rely on short passwords that you can remember and type easily. The longer the password, the harder it is to crack. A password of 16–20 characters is generally considered safe; never use anything shorter than 13 characters.
- Even if one of your passwords was compromised, having a different password for every site ensures that the attackers can’t break into any of your other accounts.
But password security hasn’t always been a big deal on the Internet, and many people reused passwords regularly in the past. Wouldn’t it be nice to know if any of your information was included in a data breach, so you’d know which passwords to change?
A free service called Have I Been Pwned does just this (“pwned” is hacker-speak for “owned” or “dominated by”—it rhymes with “owned”). Run by Troy Hunt, Have I Been Pwned gathers the email addresses associated with data breaches and lets you search to see if your address was stolen in any of the archived data breaches. Even better, you can subscribe to have the service notify you if your address shows up in any future breaches.
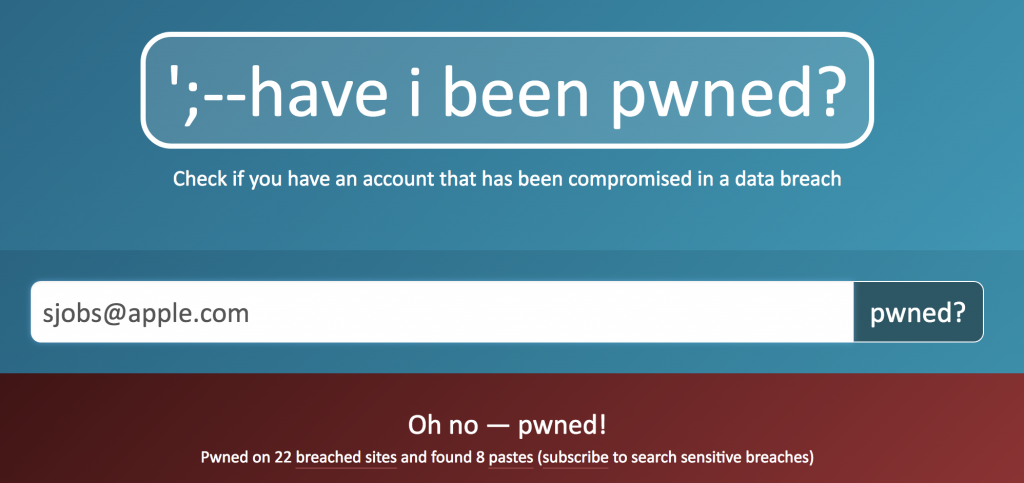
Needless to say, you’ll want to change your password on any site that has suffered a data breach, and if you reused that password on any other sites, give them new, unique passwords as well. That may seem like a daunting task, and we won’t pretend that it isn’t a fair amount of work, but both 1Password and LastPass offer features to help.
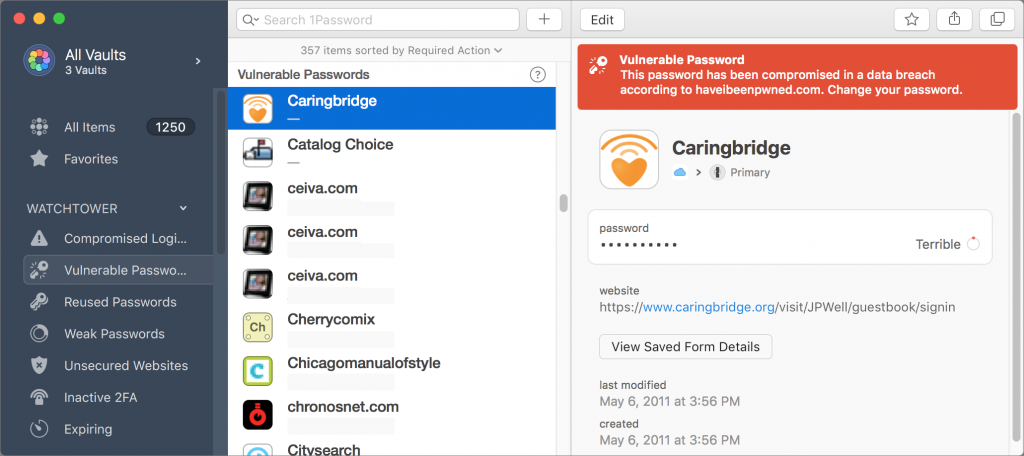
In 1Password, look in the sidebar for Watchtower, which provides several lists, including accounts where the password may have been compromised in a known breach, passwords that are known to have been compromised, passwords that you reused across sites, and weak passwords.
LastPass provide essentially the same information through its Security Challenge and rates your overall security in comparison with other LastPass users. It suggests a series of steps for improving your passwords; the only problem is that you need to restart the Security Challenge if you don’t have time to fix all the passwords at once.
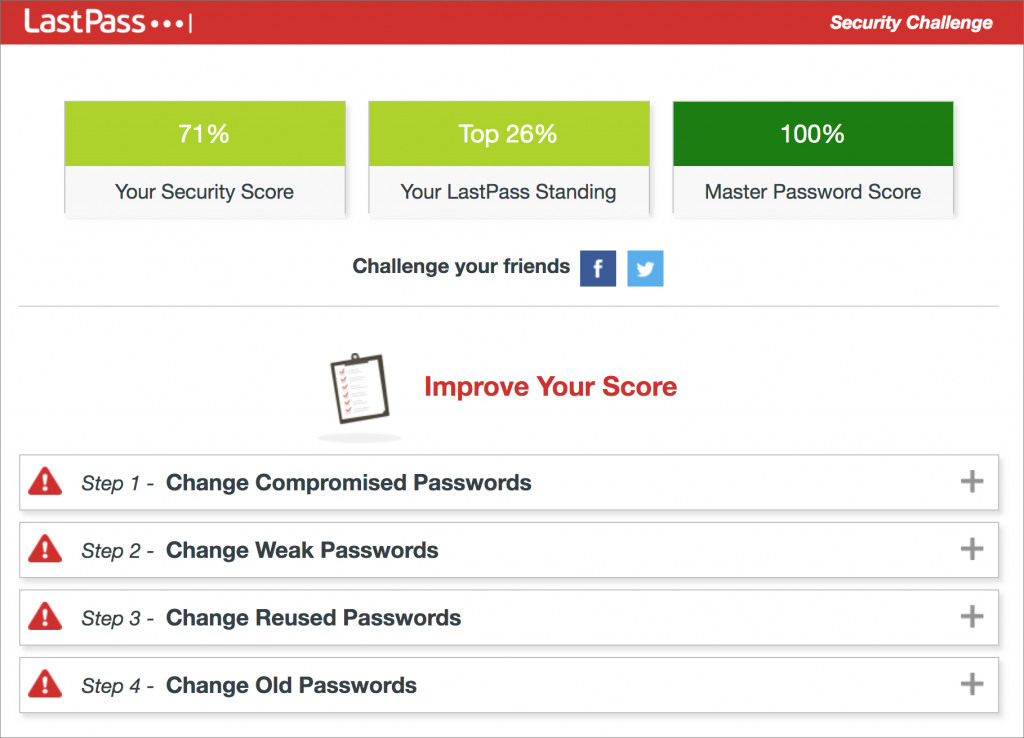
Regardless of which password manager you use, take some time to check for and update compromised, vulnerable, and weak passwords. Start with more important sites, and, as time permits, move on to accounts that don’t contain confidential information.
Super Bad Apple Vulnerability
Hey –
Just wanted to give a heads up that anyone who is one of our support customers can sleep soundly tonight.
Within minutes of reading the breaking news of todays “Root” vulnerability, we had automagically patched all of the “Pro” and Total” support customers machines that were exposed to the vulnerability.
Want some numbers? Ok. Across our fleet of Pro and Total Support users (about 300ish), only 6 machines were vulnerable (2 of them were in our test lab) And by 4:00 pm today, we had a tested and pushed out a fix to all 6.
Why only 6 when we have 100’s under care? Well, thats because we carefully manage macOS and system updates, and except in extreme cases, we have been actively blocking user installs of Mac OS 10.13 High Sierra.
How bad is this vulnerability? Its bad, but someone would need to have access to your computer to do harm. We imagine that Apple will fix it quickly. And likely silently without user intervention.
Of the 300+ users that are on our Basic support plan, about 20 of them had been ignoring our “hold off on upgrading” warnings. Those users had emails in their inboxes within an hour or so that described the steps they needed to take to secure their machines.
Want some more info on the vulnerability?
Here’s what Apple had to say…
“We are working on a software update to address this issue, In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here: https://support.apple.com/en-us/HT204012. If a Root User is already enabled, to ensure a black password is not set, please follow the instructions from the ‘Change the root password’ section.”
From AppleInsider
“Discovered earlier today, the flaw allows anyone to log in under a Mac’s “root” System Administrator without the need for a password. In practice, the exploit merely requires access to System Preferences, and can be performed in a matter of seconds. Nefarious users can also exploit the bug to bypass a Mac’s lock screen.
Beyond those who have direct access to a vulnerable Mac, the security hole also works remotely in certain scenarios where screen sharing, remote access or VNC sessions are enabled. Users should disable those features until Apple’s update arrives.
As AppleInsider reported when the vulnerability was first aired today, macOS High Sierra users can prevent unauthorized Mac access by disabling the Root User under System Preferences. Alternatively, and as Apple suggests, users can enable the Root account and set a password.
Apple failed to provide a release timeline, but considering the bug impacts system-level directories and is relatively easy to exploit, a software update should be out soon.“
Heartbleed and you
Heartbleed: What does it mean to you.
These are scary times, but we have some advice, and have compiled places below where you can go for more info.
By now you have seen the news, probably had people ask you if you were changing all your passwords, and are wondering if you should be freaking out.
We try to keep people from freaking out, but we do think you should changes some passwords, and in general follow some of our password advice.
There are a couple of really important things to keep in mind.
- While the Heartbleed vulnerability has gone undetected for a very long time, there are no known exploits or data losses. However, by the nature of the exploit, it is impossible to tell so its good be careful and vigilant.
- Changing your password on unpatched servers does not make you safe. Its important to wait until a server has been patched before you change your password.
- If you get a legit message from a service that you use asking you to change your password, please heed their advice. But also, beware of phishing scams. Bad people are out there and they will try to exploit your confusion. Be sure you are making changes on the legit site and not being scammed.
Below is a quick list of common services many of our clients use that have been patched that require password changes. If you use these services, go now and change your password. And, if you us that same login and password someplace else, you need to change your password there as well for safety.
- Dropbox
- Google Apps
- Pintrest
- Yahoo/Yahoo Mail
- Rackspace Mail
- Media Temple
- GoDaddy
- GitHub
Creativetechs Password Advice
Use a Password Manager (Keychain, 1Password, etc.)
Use different passwords everywhere. Yes this is difficult, but that is why we recommend a password manager.
Use complicated passwords. There is a ton of advice about how to create a complex password. (See links below) Just know that the longer the better, mix in Upper/lower case, add in some numbers or other characters.
Some useful links.
Heartbleed checker. Drop a url in here and see if the site you are visiting is safe.
The Heartbleed Hit List. Passwords you need to change right now.
Heartbleed explained in a video.
I Need Your Support! Please Comment.

I’ve got a special request this week. Jason and I are working on our next big online course. If you’ve ever gotten something out of an online class from Creativetechs, we need your help now.
I’m hoping you’ll take the time to answer three questions in the comments below:
1. What makes the Creativetechs training approach different?
(How does our class format compare to local classes, training videos, or other online webinars?)
2. Where do you live?
(We want to demonstrate the size of our audience with the comments on this post. Tell us where you live, and what time of day you join in for class.)
3. Does this live worldwide format really work?
(This is the important part. What does the experience feel like to you? Can you help describe this format to someone who’s never seen it?)
We’re planing an ambitious 6-month Photoshop course that builds from basics into advanced retouching techniques. To pull it off, we need new space, faster Internet, and some key partnerships. I’m talking with people this week, and I want to point skeptics among them to your comments to demonstrate that this online training format works.
We need your testimonials to help entice experts to Seattle for our little worldwide classroom. And I need to demonstrate the reach of our current classes in order to attract the support and sponsorship we’re going to need to keep this live class experience free.
Thanks!

PS. Scroll down to a comment I posted over the weeekend for my boldest public declaration so far about where we’re going with our online classroom. Scary and Exhilarating!
PS2. I’ve been updating and revising this post all weekend. So if early commenters don’t seem to be responding to the same questions, that’s MY fault, not theirs. 🙂
Seattle Help Wanted: Simple Video Production.

Okay, I need help. Our online classes are really taking off, and before our new 10-Week Flash Course starts next month, we need someone helping record and edit the videos for each class.
What does the job entail?
This person needs to arrive about 90 minutes before class starts to test all the sound and video feeds. They need to oversee the video and audio recording during class. After class, they need to lightly edit the final recording, and prepare final video files to be uploaded on the web.
We’re currently looking for 1-or-2 people who can handle these tasks as we continue to add additional courses to our weekly schedule.
This person should be experienced supporting various video and audio setups, very computer savvy, experienced with Final Cut Pro and other editing tools. And most importantly, reliable and trustworthy.
A bonus would be finding someone with web production skills who can update online course pages with the newly uploaded videos.
If you are interested, please email training@creativetechs.com. You should come in and watch one of our live classes in action, and we can discuss the options. I’d like to start interviewing people after this Thursday’s InDesign class (10:30am – 1:00pm), so please help spread the word.
PS. This is a paid position, however I’m not sure what it should pay. It is certainly not a full-time position (although the way things are growing around here, you never know!)
Introducing the new Make Mac Work
 Make Mac Work is our sister blog focused on helping people who manage Macs in larger Enterprise environments. We’ve been working behind the scenes, and today we’re unveiling a clean new look to the site:
Make Mac Work is our sister blog focused on helping people who manage Macs in larger Enterprise environments. We’ve been working behind the scenes, and today we’re unveiling a clean new look to the site:
Jordan has updated most of the article archives for Mac OS 10.5 Leopard. For a sense of this site’s technical focus, browse through some of the essential articles:
» Deploy Portable Home Directories
» Master Open Directory
» Configure Network Installation
» Manage Account Preferences
» Control Software Update
» Bind to Active Directory
If you are an IT professional who is responsible for supporting Macs, this website is a resource you’ll want to bookmark.
Creativetechs Brings Home the Bacon!

Wow. We had a fantastic Photoshop class today!
Today we experimented with adding a live Twitter chatroom for webinar participants to interact with each other during the workshop. That was a lot of fun, and in the process #creativetechs ended up becoming a trending topic on Twitter’s search page.
That’s largely thanks to an extended Twitter conversation about bacon. Which ended up spilling out into the live classroom. (Don’t worry, that will become clear once we get some video clips posted.)
Today was a LOT of fun. Thanks to everyone in person and online who joined us.
Feedback Wanted: Make Mac Work.
 This is a bit off-topic from our tips format. I’d like to put out a request to the more technical readers in our audience. Our lead enterprise engineer, Jordan Bojar, has been asked to pull together a book proposal based on his Make Mac Work blog.
This is a bit off-topic from our tips format. I’d like to put out a request to the more technical readers in our audience. Our lead enterprise engineer, Jordan Bojar, has been asked to pull together a book proposal based on his Make Mac Work blog.
If you have never visited, Make Mac Work is our sister blog covering IT issues facing Macs in Enterprise environments. If that sounds interesting, you can browse some of the essential articles in the blog archives:
» Portable Home Directories
» Master Open Directory
» Configure And Deploy NetInstall
» Manage Account Preferences
» Control Software Update
» Bind to Active Directory
If you are an IT professional who is responsible for supporting Macs in larger corporate networks, I’d recommend you bookmark this blog. And we’d appreciate any feedback or suggestions you might be willing share to help Jordan flesh out his book proposal.
Thanks.
Quote From Last Night’s AdWords Class.
I teach monthly online marketing seminars at our Seattle training partner Luminous Works. Last night I led a new class on Google AdWords & Online Advertising. There will be tips from that class coming up in future weeks, but I wanted to share a quote from an email I received this morning from one of last night’s attendees:
“Craig, This was a GREAT class. The informal and succinct presentation provided simple and manageable solutions to what for most is mind-numbingly complex material. Best of all, I can implement 90% of your recommendations myself. In short, a comprehensive class in very professional and comfortable surroundings… worth 10X the price! I would recommend the class for anyone — except my competitors!” – Alan Burke, Classic Nursery & Landscape Company
Before anyone asks, yes, one day we’ll offer these online marketing classes via our workshop/webinar format. Probably not for several months however.




