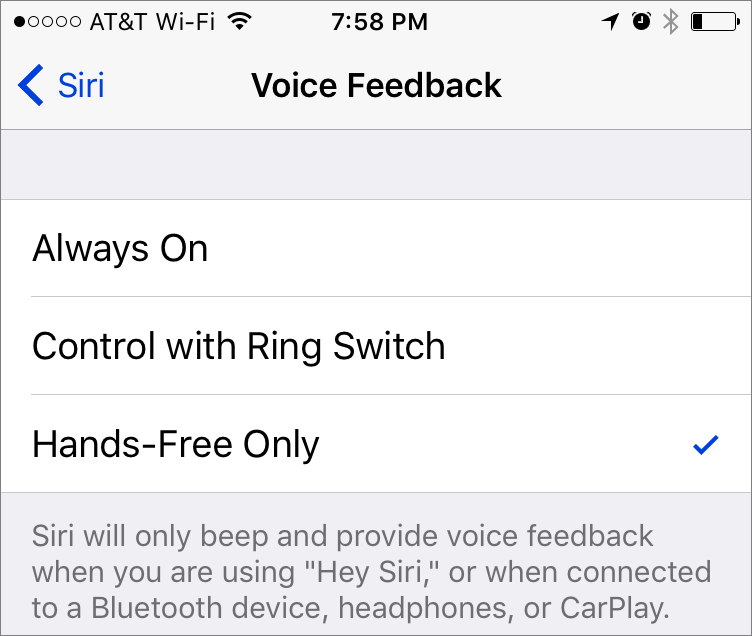
By default, Siri likes to chat, confirming what you say and speaking the results of your commands when appropriate. If you don’t like that, go to Settings > Siri > Voice Feedback and select either Control with Ring Switch (the iPhone’s physical switch) or Control with Mute Setting (iPad) to make Siri be quiet when the device is muted. Alternatively, choose Hands-Free Only to silence Siri except when connected to Bluetooth, headphones or CarPlay. Or set Siri to whisper—hold the Home button to invoke Siri and then reduce the volume, which applies only to Siri’s voice.











 All motion on the screens of both iPad Pros will be smoother and more responsive, thanks to a previously unheard of 120 Hz refresh rate. It will make drawing with the Apple Pencil even more fluid. The screens are also brighter, can display more colors, and have low reflectivity. Both models get new cameras that match those in the iPhone 7: a 12-megapixel rear-facing camera with optical image stabilization and True Tone flash, plus a 7-megapixel FaceTime HD camera on the front.
All motion on the screens of both iPad Pros will be smoother and more responsive, thanks to a previously unheard of 120 Hz refresh rate. It will make drawing with the Apple Pencil even more fluid. The screens are also brighter, can display more colors, and have low reflectivity. Both models get new cameras that match those in the iPhone 7: a 12-megapixel rear-facing camera with optical image stabilization and True Tone flash, plus a 7-megapixel FaceTime HD camera on the front.