Get Your Tech Gear Ready to Travel this Summer
Planning a vacation this summer? A little tech prep can help ensure that your devices don’t let you down while you’re away. We have advice for what to bring, essential apps, and more.
Improve Google Chrome Security with these 2 Techniques
If you use Google Chrome or another Chromium browser instead of Safari, you can stay secure by following two simple rules regarding updates and extensions.
Are your employees reporting security issues fast enough… or even at all?
The faster your employees report a potential cyber security issue, the less damage is done to your business. But how can you encourage quick reporting? Here we share some solid ideas.
You might hold the secret to data security in your finger
Is your password keeping your data as safe as it could be? Maybe not. And there are new, safer alternatives to try. Here are all the details.
More businesses are proactively investing in cybersecurity defenses
Your business data is valuable, and protecting it means safeguarding your business’s operations and reputation.
Give Your Team Access to a Single Account by Sharing 2FA Setup
For better results when a team or family group needs to share 2FA codes to log in to a website, try to use an authentication app instead of SMS, or better yet, use a password manager that can both generate 2FA codes and share logins with a group.
It’s Quite Possible Apple’s iCloud Keychain Password Management Can Handle All Your Needs
Apple’s iCloud Keychain password manager keeps improving, and we now recommend it, especially for those not already using a third-party password manager. Here’s how to use iCloud Keychain to store and enter secure passwords.
Uh oh! You’re at greater risk of malware than ever before
Small and medium-sized businesses are at more risk of a malware attack than ever. It’s time to take action to protect your business. Here we tell you how.
Cybersecurity training once a year isn’t working
You’re wasting your time on annual cybersecurity training. Why? Because it’s simply not cutting it anymore. Discover a better plan here.
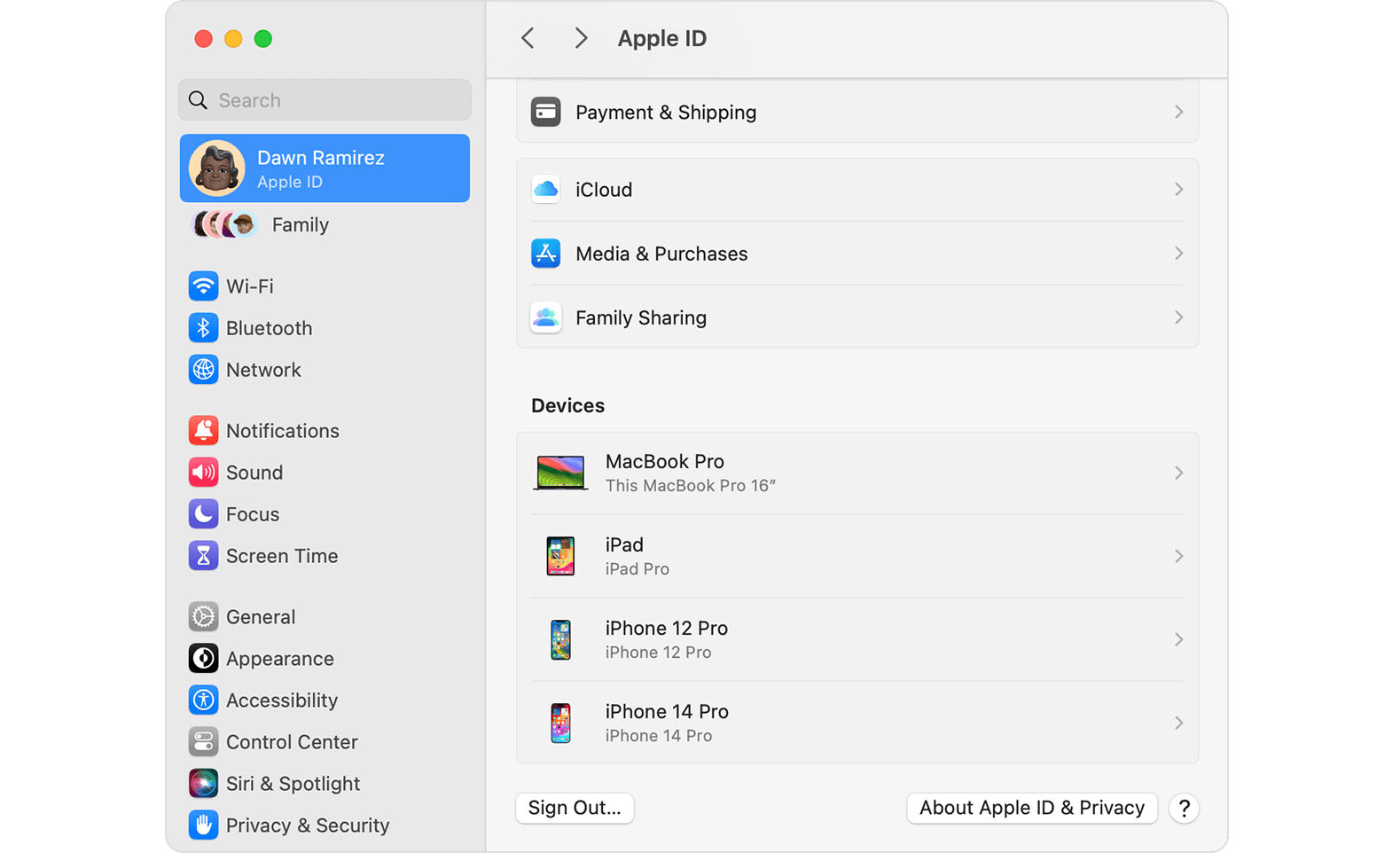
Improve Security by Auditing Your Trusted Device Lists
We all accumulate “trusted devices” in our Apple, Google, and password manager accounts, but it’s important to remove devices you no longer use because they could be security risks.