Best wishes for a happy holiday season and our sincere thanks for your loyalty and goodwill throughout the year.

Best wishes for a happy holiday season and our sincere thanks for your loyalty and goodwill throughout the year.

orem ipsum dolor sit amet, consectetur adipiscing elit. Sed iaculis purus euismod tortor luctus, eget scelerisque quam suscipit. Sed ullamcorper diam et urna hendrerit scelerisque. Donec elementum sapien molestie dolor feugiat, at vehicula orci suscipit. Nam elementum eu risus at ullamcorper. Curabitur malesuada urna nec sem venenatis consequat. Duis nec mollis mi. Cras condimentum, ipsum non varius pulvinar, libero elit laoreet felis, id venenatis sem nibh et risus. Vestibulum bibendum id nulla sit amet blandit. Ut et ultricies eros. Etiam et quam porta, commodo urna ac, faucibus enim. Nunc suscipit enim sed leo dignissim tincidunt.
Quisque varius sollicitudin lacus non auctor. In velit risus, imperdiet hendrerit erat ac, sollicitudin tristique nisl. Curabitur a hendrerit sem, at imperdiet purus. Aliquam convallis, dui ac eleifend fermentum, risus tellus consectetur dolor, non semper magna purus in arcu. Vivamus tempus tristique enim, quis mattis ante rhoncus vulputate. Suspendisse sit amet accumsan mi. Praesent ultricies augue in luctus molestie. Vivamus felis dui, posuere at rhoncus eu, tempus sit amet velit. Cras faucibus diam et consectetur porttitor.
Nunc quis felis eu urna laoreet ornare. Donec vehicula placerat lectus, luctus finibus massa cursus malesuada. Sed ac laoreet dolor, ac lacinia sapien. Proin mi massa, placerat ac erat dictum, dictum rhoncus libero. Sed sed volutpat lacus. Suspendisse vulputate, lectus id ornare posuere, magna mi sodales dolor, a ultricies justo lacus eu dolor. Pellentesque et libero a eros consequat pellentesque non in eros. Curabitur ut erat justo.
Phishing scammers are getting more and more sophisticated. You no longer have to only watch out for misspellings or fraudulent emails coming from your “IT Department.” Of course, these are still things to concern yourself with and be on the lookout for but the attacks are becoming more and more difficult to detect.

CEO’s and CFO’s Targeted
In recent weeks, there have been two cases of phishing scams that are otherwise undetectable. Not only are they more difficult to spot but they are going to more powerful people in businesses. Scammers took the time to research organizational structures so they not only would know who to contact but they also know who to impersonate. In the most recent cases, the cyber attackers used the internet to determine the organizational structures and who the CEO’s or CFO’s were. They then took the time to research board members and other senior employees who would have interaction with the intended target. This kind of implementation went even further because they found legitimate reasons for the board members or senior employees to request funds. They then sent the email to the intended victim and asked for money for a completely plausible need. The attacks were very well researched and thought out. They were even executed in a way that it was almost impossible to detect. There were no red flags with the emails and it was essentially the perfect implementation.
Protecting Yourself Against Phishing Attacks
Even though the nature of phishing attacks is changing rapidly, you still need to watch out for the most basic components of one to better protect yourself. In addition to the rules that many people already know, there are new things to be aware of. These are just some of the things to look out for:
For more information on how you can better protect yourself from potential phishing scams in {city}, be sure to contact {company} by calling us at {phone} or emailing {email}.
Optimizing your technology for success in business won’t happen by accident. Achieving an efficient and effective IT environment requires time, expertise, structure and a proven strategy tailored to your needs, all of which you can get from our IT Experts.

We’re Urging Local Individuals and Businesses to be Informed about Latest and Most Sophisticated Cyber Scam
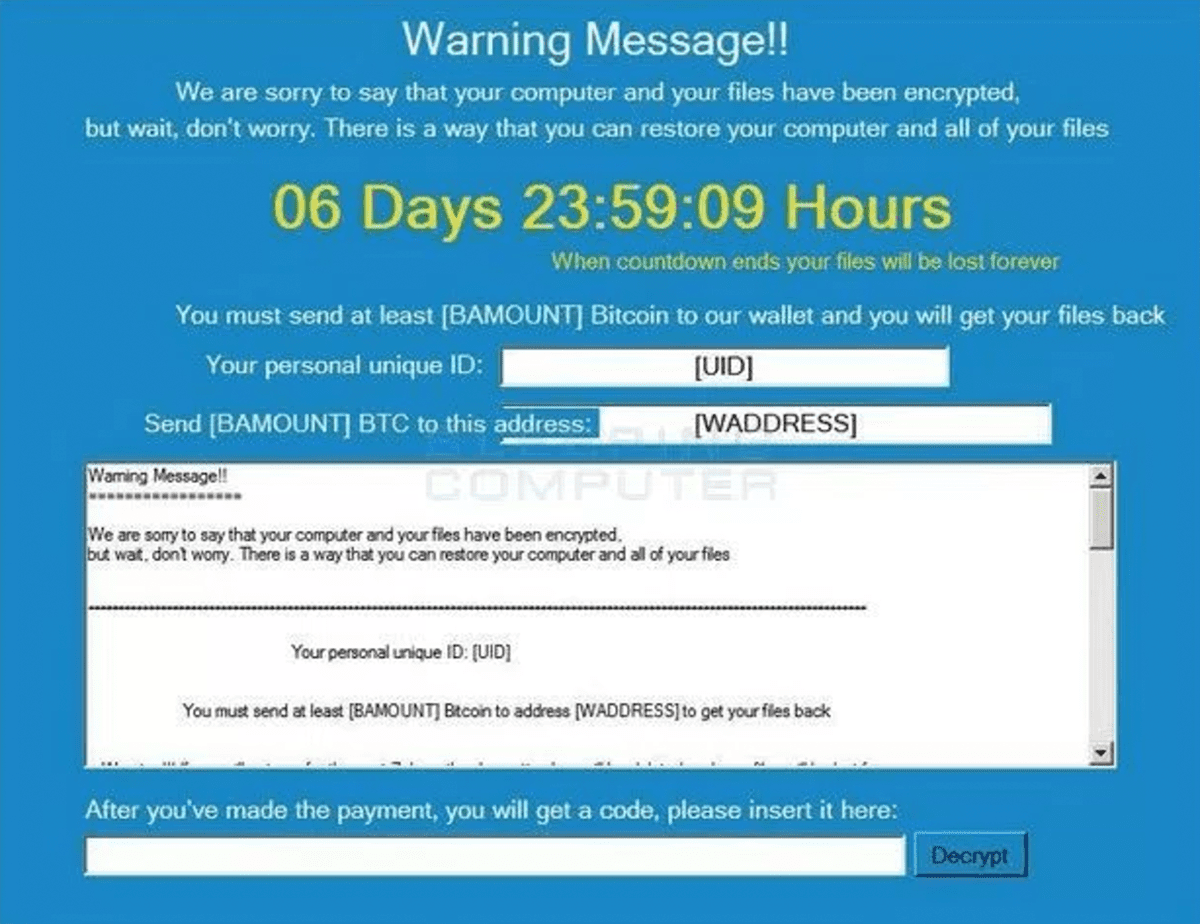
The need for cyber security has been on the radar and in the playbooks of serious companies and their executives for some years. However, recent advancements in a particularly virulent strain of software called “ransomware” has made even forward-thinking CIOs sit up and take notice. Ransomware attacks are hitting individuals, institutions and businesses hard, right here in {city}. Ransomware attacks are defined by their demand for incredibly high ransom fees simply to restore access to information and reinstate productivity.
As if that wasn’t bad enough, the newest form of diabolical ransomware floating around the internet is through a software called Popcorn Time. Popcorn Time is deviously named after but unrelated to the bittorent piracy app and quickly infects a user’s machine and demands a 1 bitcoin ransom (over $700), to reinstate access to data held hostage. However, the particularly daunting aspect of this strain of ransomware is the alternative escape option it offers. If an infected user can’t afford the bitcoin payment, they can have their files released for free on one condition: send the malicious link to two friends, have them download the infection and pay the ransom.
Reminiscent of a B-rated Hollywood horror film or a bad pyramid scheme, this new method of spreading the virus and seeking out more victims is incredibly hard to track, prevent and slow down. The frightening new software was discovered by cyber-security researchers, MalwareHunterTeam, and the malicious program is still in development. However, researchers claim that if left to develop fully, the innovative method of distribution could make Popcorn Time one of the most dangerous and wide-spread cyber-scams on the internet.
So what can individuals do to stay protected? And what does one do when they find themselves faced with paying a ransom or selling out their friends? The cyber-security experts at {company} want to make sure {city} individuals and businesses are well-versed in how to proactively keep data protected before nasty ransomware like this takes hold of data. The most important point of defense is securing reliable back-up solutions where an emergency copy of all important data is stored and protected on a separate machine or in the cloud.
Through proactive and strategic planning and preparedness, the {company} team is committed to ensuring that their client base is equipped with comprehensive back-ups in case of attack or disaster. Because of this foresight, {company} clients wouldn’t have to pay the ransom to retrieve their files in the case of an attack, nor would they have to consider selling out colleagues or friends to avoid the bitcoin payment.
Even with backups in place, damage-control and restoration time to get business back on track can be costly. Though the {company} team is equipped to help clients recover from disaster quickly, there is a cost associated for the man hours needed to restore data. Not to mention the lost productivity and wage expenses that businesses suffer because their employees are unable to work for a certain amount of time. Furthermore, ransomware attacks like Popcorn Time are getting increasingly sophisticated and malicious and can manifest in ever-evolving ways. Therefore, it’s critical to have a variety of cyber-security measures in place to ensure protection.
Investing in the correct preparation and protection mechanisms may seem time consuming or costly, however, the cost pales in comparison to the potential damages that a ransomware attack can cause. As the prevalence and sophistication of ransomware continues to rise, the potential cost and productivity savings of enlisting IT support is becoming increasingly evident.
If you’d like to connect your business-minded audience with more information about this nasty new strain of Ransomware, other daunting cyber-security threats and tips for staying informed and protected, please don’t hesitate to reach out to {company} at {phone} or email us at {email}.
Keeping the masses informed is the first and most important step against beating cyber criminals.