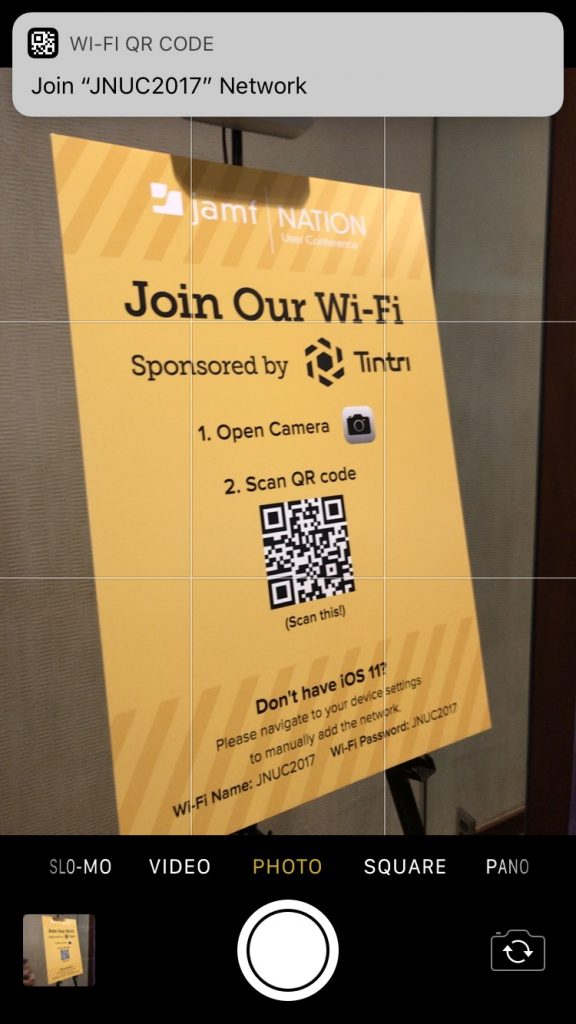
You’ve undoubtedly seen those odd-looking square QR codes on product packaging, a business card, or a flyer. In the past, you needed a special app to scan a QR code to see what Web URL, contact card, Wi-Fi network, or other piece of information it held. In iOS 11, though, you can just point your iPhone or iPad camera at a QR code—no need to take a picture! Then tap the notification that appears at the top of the screen to display whatever data was encoded by the QR code.